AI-powered Security Services
At LeewayHertz, we empower enterprises to stay ahead of evolving threats through AI-powered security services that unify AI-driven cyber defense and secure AI engineering. Our approach bridges innovation and assurance to build, test, and deploy secure AI systems that safeguard digital ecosystems, fortify models and data pipelines, and deliver trusted, scalable protection. By embedding security into every layer of the AI lifecycle, we reinforce trust, governance, and operational excellence across the enterprise.
Trusted By Leading Enterprises


AI Developers
Software Products Delivered
AI Solutions
Total Years of Experience
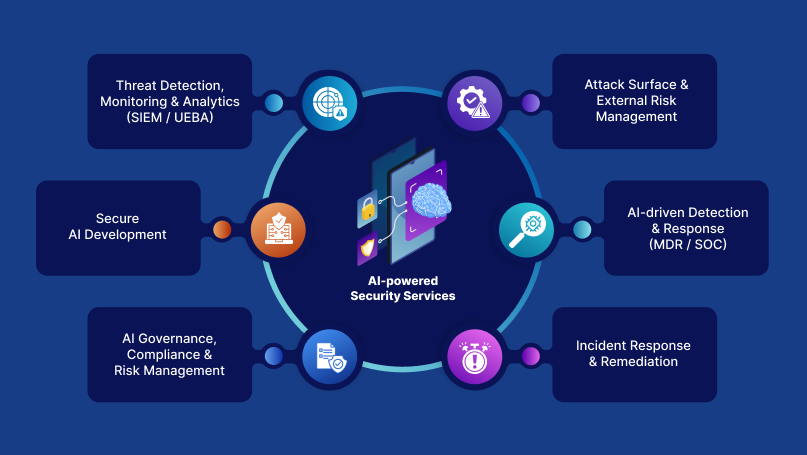
Our AI-powered Security Services
As an enterprise-grade AI security services company, we deliver a unified portfolio of cybersecurity & AI security services designed to reduce risk, accelerate detection, and improve decision-making. Each engagement is tailored to your infrastructure, compliance frameworks (ISO 27001, NIST CSF, SOC 2), and enterprise maturity—delivering measurable, business-aligned outcomes.
Managed Security & Operations

Managed Detection & Response (MDR)
We use AI-driven analytics and behavioral modeling to detect, investigate, and contain threats in real time. Automated workflows identify attacks early, reduce false positives, and accelerate incident resolution.

SOC (Security Operations Center)
We provide a 24×7 AI-enhanced SOC that delivers continuous monitoring, intelligent triage, and actionable insights—without expanding your internal team.

NOC (Network Operations Center)
We apply predictive analytics, deep packet inspection, and anomaly detection algorithms to ensure early-stage DDoS indicators and optimal uptime.

Cloud & IT Security Operations
We deliver visibility and configuration monitoring across hybrid and multi-cloud environments, identifying misconfigurations, privilege escalations, and data exposures before exploitation.
Detection, Monitoring & Analytics

SIEM (Security Information & Event Management)
We enhance your SIEM with AI correlation, alert enrichment, and prioritization. Our solutions can analyze large volumes of telemetry to uncover hidden threats and accelerate incident resolution.

UEBA (User & Entity Behavior Analytics)
We build machine learning models to baseline user and entity behaviors and detect anomalies. Our models help reduce false positives while improving detection accuracy for insider and lateral threats.

Threat Intelligence
We enrich threat feeds using AI-powered analytics and predictive scoring. By correlating indicators of compromise (IOCs) with real-time telemetry, we help your teams anticipate threats and prioritize response.
Security Automation

SOAR (Security Orchestration, Automation & Response)
We implement automation and orchestration playbooks that centralize alerts, coordinate response actions, and accelerate incident containment. By integrating across your security stack, we reduce noise, eliminate repetitive tasks, and drive faster, more effective remediation.

AI Agents for Security Operations
We build and implement SOC support agents that streamline key workflows, including incident triage, summarization, remediation recommendations, and ticket lifecycle management, reducing workload and improving response consistency.

Intelligent Analyst Copilots
We engineer custom copilots that enhance detection, investigation, and reporting through automated analysis and contextual insights. They enrich alerts, generate executive summaries, and preserve institutional knowledge for faster, more informed decisions.
Vulnerability Management & Testing

Vulnerability Management
We run AI-enhanced scanning and prioritization to focus on the most exploitable risks. We apply contextual threat intelligence to predict exploitability and automate patch workflows, reducing your exposure window and strengthening overall defence.

AI Penetration Testing
We combine human red teaming with AI-augmented reconnaissance and attack simulation. We identify vulnerabilities more quickly and validate controls under real-world stress.

Exposure Management
We continuously monitor for misconfigurations, shadow IT assets, and exposures using AI. We drive proactive remediation with prioritized insights.
Attack Surface & External Risk

Attack Surface Management (ASM)
We continuously discover and classify external assets, domains, and services using AI-driven asset discovery and DNS monitoring. We keep you aware of your digital perimeter and prevent exposure and exploitation.

External Risk Management
We evaluate third-party and supply chain risks to uncover hidden vulnerabilities, improve transparency, and guide proactive mitigation strategies across your extended enterprise.
Incident Response & Remediation

Incident Response
We deploy AI-enhanced detection, containment, and analysis workflows for rapid breach response. We uncover root causes faster and minimize impact.

Remediation Services
We orchestrate cleanups, patching, and hardening with automated, traceable workflows- restoring system integrity while embedding continuous improvement.

Readiness Assessment
We simulate scenarios using AI models to test your backup, recovery and resilience strategies—identifying weak links and strengthening recovery readiness.
Strategy, Risk & Assessments

Cyber Risk Assessment
We quantify enterprise exposure using AI-based probabilistic risk modeling. Our dashboards translate technical metrics into business impact KPIs for informed decision-making.

SecOps Readiness
We benchmark maturity across your team, processes, and tooling. We identify gaps in tooling alignment, process consistency, and talent readiness for AI-enhanced operations.

AI Red Team
We simulate adversarial attacks against AI and LLM systems using prompt injection, perturbation, model inversion, and more. We validate model robustness against manipulation, ensure fairness across inputs, and strengthen overall system resilience. Our methodology applies adversarial machine learning, gradient-based evasion, and token-level prompt injection testing.

Secure AI / LLM Assessments
We assess AI/LLM systems end-to-end—threat modeling, prompt injection resistance, data leakage, pipeline security, and privacy controls. We implement guardrails and secure pipelines for safe, enterprise-grade model deployment.
AI-powered Security Solutions We Deliver
We engineer tailored, enterprise-grade AI security solutions that embed protection at every layer of your digital ecosystem.

AI-driven detection systems

Copilots

Autonomous Agents & Assistants

Risk & Exposure Intelligence Dashboards
Why Choose Our AI-Powered Security Solutions?

Dual AI Advantage

Full-stack Expertise

Outcome-driven

Scalable & Adaptive

Trusted by Enterprises

Regulatory & Framework Alignment
Why Partner With LeewayHertz for AI-powered Security Services

Extensive Industry Experience

Diverse Expertise

End-to-end Delivery Capability

Enterprise-grade Delivery

Trusted Technology Partnerships

Innovation With Assurance
Our Delivery Approach
At LeewayHertz, we follow a structured, outcome-focused approach to deliver secure, scalable, and intelligent solutions tailored to each client’s needs.

Discovery & Assessment

Design & Planning

Implementation & Integration

Validation & Optimization

Continuous Support & Enhancement
Big Brands Trust Us

Our Artificial Intelligence Portfolio
Generative AI Application
LLM-powered App for Compliance and Security Access
Data Analysis
Geospatial Data Analysis
AdPerfect: AI-powered SaaS Platform for Advertisement Generation
As Mentioned in


Our Engagement Models

Dedicated Development Team
Our developers leverage cutting-edge cognitive technologies to deliver high-quality services and tailored solutions to our clients.

Team Extension
Our team extension model is designed to assist clients seeking to expand their teams with the precise expertise needed for their projects.

Project-based Model
Our project-oriented approach, supported by our team of software development specialists, is dedicated to fostering client collaboration and achieving specific project objectives.
Get Started Today
1. Contact Us
Fill out the contact form protected by NDA, book a calendar and schedule a Zoom Meeting with our experts.
2. Get a Consultation
Get on a call with our team to know the feasibility of your project idea.
3. Get a Cost Estimate
Based on the project requirements, we share a project proposal with budget and timeline estimates.
4. Project Kickoff
Once the project is signed, we bring together a team from a range of disciplines to kick start your project.
Start a conversation by filling the form
All information will be kept confidential.
Insights
Generative AI in asset management: Redefining decision-making in finance
Generative AI is reshaping asset management by incorporating advanced predictive capabilities, fundamentally altering decision-making in finance for more informed investments.
Generative AI in supply chain: Use cases, benefits and development
Incorporating generative AI promises to be a game-changer for supply chain management, propelling it into an era of unprecedented innovation.
From diagnosis to treatment: Exploring the applications of generative AI in healthcare
Generative AI in healthcare refers to the application of generative AI techniques and models in various aspects of the healthcare industry.
 Detection, Monitoring & Analytics
Detection, Monitoring & Analytics Security Automation
Security Automation Vulnerability Management & Testing
Vulnerability Management & Testing Attack Surface & External Risk
Attack Surface & External Risk Incident Response & Remediation
Incident Response & Remediation Strategy, Risk & Assessments
Strategy, Risk & Assessments





