Identity, Email and Access Security
LeewayHertz helps enterprises safeguard their digital identities, communication channels, and privileged access through a comprehensive suite of security services. From IAM strategy and privileged access governance to identity threat detection and phishing resilience, we empower organizations to protect the most targeted layers of their security ecosystem. Our solutions ensure secure access, detect malicious behavior in real time, and build resilience against modern threats across cloud and hybrid environments.
Trusted By Leading Enterprises


AI Developers
Software Products Delivered
AI Solutions
Total Years of Experience
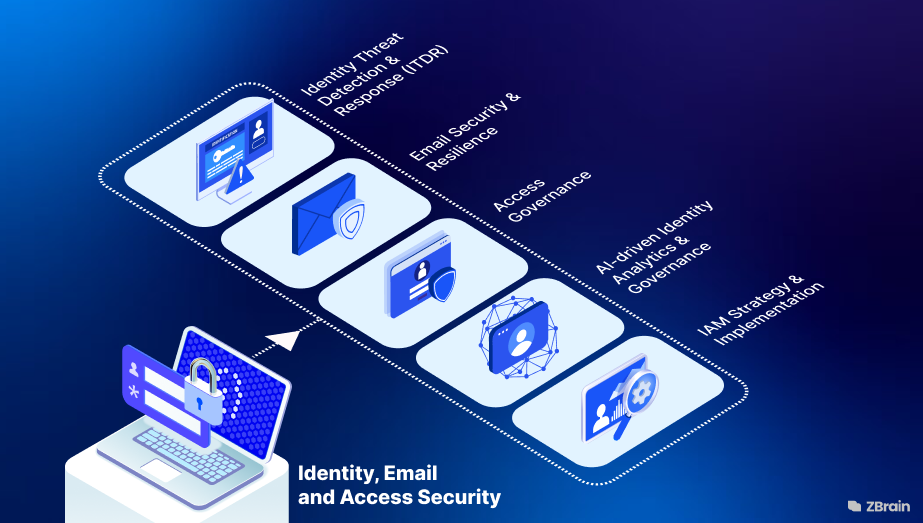
Our Comprehensive Identity, Email and Access Security Services for Enterprises
LeewayHertz helps enterprises protect digital identities, secure access, and defend communication channels through intelligent, AI-driven security.

IAM Strategy & Implementation

Identity Threat Detection & Response (ITDR)

Privileged Access Governance

Email Security & Resilience

Access Governance

AI-driven Identity Analytics & Governance
Enhance Resilience With Our Identity, Email, and Access Security Services

Enhanced Identity Resilience

Operational Efficiency

Scalable, Future-ready Security

Strengthened Stakeholder Trust

Accelerated Compliance and Audit Readiness

AI-driven Intelligence and Automation
How We Deliver Identity, Email, and Access Security
LeewayHertz takes a strategic, intelligent approach to identity, email, and access security — combining governance and automation to protect the most targeted layers of enterprise ecosystems.
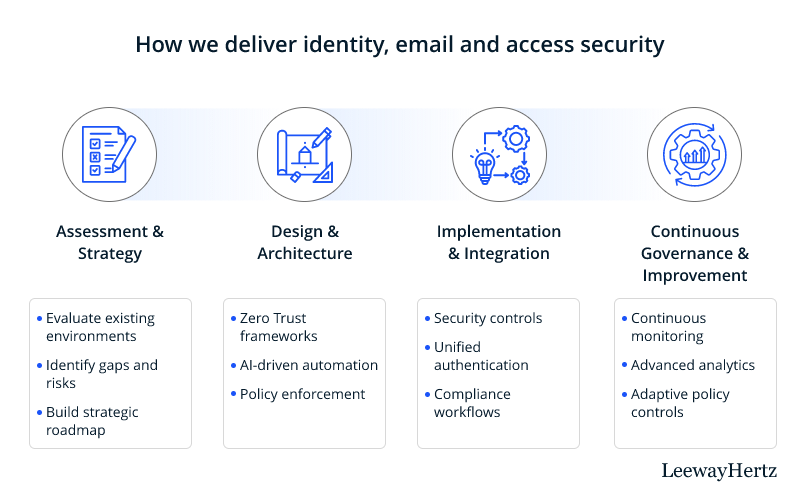

Assessment & Strategy

Design & Architecture

Implementation & Integration

Continuous Governance & Improvement
Industries We Serve
We combine deep expertise in IAM strategy, access management, and email security with industry insight to help organizations protect their most targeted assets — identities, privileged accounts, and communication channels.

Banking & Financial Services

Healthcare

Manufacturing

Technology and SaaS

Insurance

Retail & E-Commerce

Telecommunications

Supply Chain & Logistics (SCM)

Pharmaceuticals
Why Partner With LeewayHertz for Identity, Email and Access Security Services
LeewayHertz combines AI innovation, deep security expertise, and technology consulting excellence to help enterprises enhance their security posture through automation, governance, and compliance. Our multidisciplinary teams and proven frameworks ensure measurable outcomes and long-term resilience.

Proven Industry Experience

Extensive Expertise

Framework and Compliance Alignment

Secure-by-Design Approach

Comprehensive Delivery Capability

Innovation with Assurance
Big Brands Trust Us

Our Artificial Intelligence Portfolio
Generative AI Application
LLM-powered App for Compliance and Security Access
Data Analysis
Geospatial Data Analysis
AdPerfect: AI-powered SaaS Platform for Advertisement Generation
As Mentioned in


Our Engagement Models

Dedicated Development Team
Our developers leverage cutting-edge cognitive technologies to deliver high-quality services and tailored solutions to our clients.

Team Extension
Our team extension model is designed to assist clients seeking to expand their teams with the precise expertise needed for their projects.

Project-based Model
Our project-oriented approach, supported by our team of software development specialists, is dedicated to fostering client collaboration and achieving specific project objectives.
Get Started Today
1. Contact Us
Fill out the contact form protected by NDA, book a calendar and schedule a Zoom Meeting with our experts.
2. Get a Consultation
Get on a call with our team to know the feasibility of your project idea.
3. Get a Cost Estimate
Based on the project requirements, we share a project proposal with budget and timeline estimates.
4. Project Kickoff
Once the project is signed, we bring together a team from a range of disciplines to kick start your project.
Start a conversation by filling the form
All information will be kept confidential.
Insights
Generative AI in asset management: Redefining decision-making in finance
Generative AI is reshaping asset management by incorporating advanced predictive capabilities, fundamentally altering decision-making in finance for more informed investments.
Generative AI in supply chain: Use cases, benefits and development
Incorporating generative AI promises to be a game-changer for supply chain management, propelling it into an era of unprecedented innovation.
From diagnosis to treatment: Exploring the applications of generative AI in healthcare
Generative AI in healthcare refers to the application of generative AI techniques and models in various aspects of the healthcare industry.






