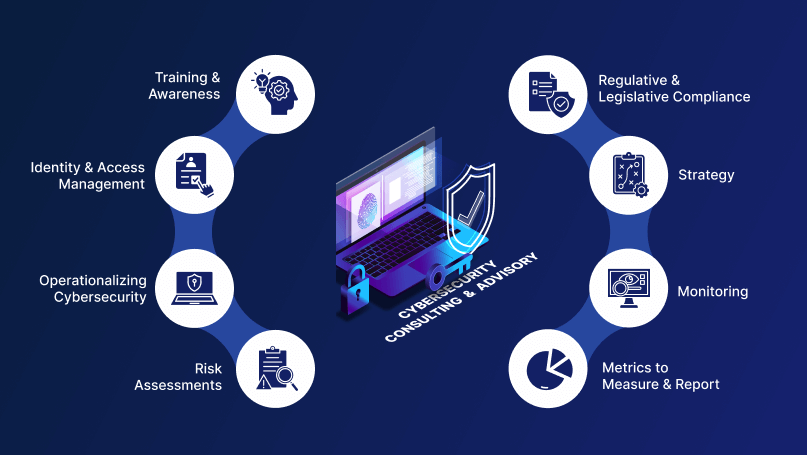
Cybersecurity Consulting and Advisory Services
We drive enterprise cybersecurity transformation through risk-based strategy, resilient architecture, and operational excellence. Our advisory services deliver structured strategy, technical execution, and continuous improvement—building resilience across governance, infrastructure, and operations. With expertise in risk management, Zero Trust, and AI-driven security, we embed protection into every layer of the enterprise to align outcomes with business objectives.
Trusted By Leading Enterprises


AI Developers
Software Products Delivered
AI Solutions
Total Years of Experience
Enterprise Cybersecurity Advisory Engineered for Strategic Impact
We deliver end-to-end cybersecurity advisory that unifies governance, architecture, and secure development. From policy frameworks and operating models to AI governance and secure DevSecOps, our approach integrates resilience, compliance, and innovation into a single, outcome-driven program.

Cybersecurity Strategy & Governance
We design and implement cybersecurity governance frameworks aligned to ISO 27001, NIST CSF, and COBIT, defining operating models, RACI structures, and board-level reporting to integrate security into enterprise risk management.
Key Services Offered:
- Defined operating models, roles, and RACI frameworks
- Policy and governance aligned to ISO 27001, NIST CSF, and regulatory standards
- Board-level risk reporting and executive dashboards
- Integration of cybersecurity into enterprise risk management

Risk, Maturity & Gap Assessments
We conduct enterprise-wide risk and maturity assessments grounded in NIST CSF, ISO 27001, and CIS Controls, translating exposure into measurable action plans. Our process integrates AI-driven risk scoring and third-party analysis to help organizations prioritize what matters most.
Key Services Offered:
- Enterprise risk and control assessments
- Cyber maturity benchmarking (NIST CSF, ISO 27001, CIS Controls)
- Third-party and vendor risk evaluations
- AI-assisted risk scoring for dynamic prioritization

Security Architecture & Zero Trust Design
We design secure-by-design architectures guided by NIST SP 800-207 and MITRE ATT&CK, applying identity-first and least-privilege principles across DevSecOps pipelines to enhance resilience across hybrid and cloud environments.
Key Services Offered:
- Zero Trust frameworks aligned to NIST SP 800-207
- Network segmentation and identity-first security controls
- Secure SDLC and DevSecOps integration
- AI-enabled design reviews and threat modeling

Cloud, Application & Data Security
We secure multi-cloud environments, applications, and data assets by hardening configurations against CIS Benchmarks, validating code and design with OWASP Top 10, and applying GDPR/CCPA-aligned privacy engineering and data governance frameworks.
Key Services Offered:
- Cloud security posture assessments (CIS Benchmarks, NIST guidelines)
- Application threat modeling and architecture reviews
- Data classification and governance frameworks
- Privacy-by-design and regulatory alignment (GDPR, CCPA)

AI Governance & Secure AI Adoption
We establish AI governance and risk frameworks aligned with NIST AI RMF and ISO/IEC 42001, defining model oversight, LLM security baselines, and adversarial testing to ensure responsible and secure AI adoption across the enterprise.
Key Services Offered:
- AI governance and usage policy development
- Model risk management aligned to NIST AI RMF / ISO 42001
- LLM security baselines and adversarial defense
- Responsible AI and AI-for-Cyber enablement

Incident Readiness & Resilience Programs
We develop and test incident-readiness and resilience programs aligned with NIST SP 800-61 and ISO 22301, combining tabletop simulations, purple-team exercises, and post-incident reviews to strengthen enterprise response capability and continuity.
Key Services Offered:
- Incident Response, BIA, and Business Continuity planning
- Tabletop and purple-team exercises
- Executive-level crisis simulation and readiness programs
- Continuous improvement through post-incident reviews and response optimization
Why Partner with Us

End-to-end coverage

Consulting + product hybrid

AI integrated by design

Outcome-driven

Standards-aligned
Our Approach to Cybersecurity Transformation
Successful cybersecurity transformation requires a structured, outcome-driven approach. Our four-phase methodology enables organizations to strengthen resilience, embed governance, and operationalize security across all layers of the enterprise.


Assess
- Baseline current posture, maturity, and risk exposure
- Conduct gap and control assessments aligned to NIST, ISO 27001, and CIS Controls
- Identify business-critical assets and prioritize high-impact risks
- Establish clear performance metrics and governance alignment

Architect
- Design the target-state security strategy, operating model, and governance framework
- Define Zero Trust and cloud security architectures tailored to enterprise needs
- Develop policy, process, and control blueprints for implementation
- Align design decisions with business priorities and regulatory requirements

Implement
- Execute the cybersecurity roadmap through coordinated initiatives
- Embed security within SDLC, DevSecOps, and operational workflows
- Deploy automation and AI-enabled controls to accelerate maturity
- Integrate security technologies and reporting into enterprise platforms

Evolve
- Continuously monitor, measure, and optimize program performance
- Conduct periodic maturity reassessments and policy reviews
- Leverage AI-driven analytics for proactive risk identification
- Drive ongoing improvement through lessons learned and governance refinement
Our Expertise
Our strength lies in the intersection of strategic consulting, technical depth, and execution excellence. We bring together cybersecurity strategists, architects, engineers, and data specialists to help organizations design, implement, and sustain resilient security programs.

Multidisciplinary Team

Proven Frameworks & Methodologies

AI-Driven Insight

Secure-by-Design Architecture

Continuous Improvement Culture

Industry & Regulatory Depth
Industries We Serve
We combine deep cybersecurity expertise with domain-specific understanding to address the unique risk, compliance, and resilience needs of each industry. Our tailored advisory services help organizations safeguard critical assets, ensure regulatory alignment, and enable secure digital transformation.
Banking & Financial Services
We help financial institutions strengthen governance, protect sensitive data, and meet evolving regulatory mandates. Our services enhance fraud prevention, payment security, and operational resilience while enabling secure adoption of digital and AI-driven finance platforms.
Retail & Consumer
Healthcare & Life Sciences
Supply Chain & Logistics

Technology & SaaS
Manufacturing
Big Brands Trust Us

Our Artificial Intelligence Portfolio
Generative AI Application
LLM-powered App for Compliance and Security Access
Data Analysis
Geospatial Data Analysis
AdPerfect: AI-powered SaaS Platform for Advertisement Generation
As Mentioned in


Our Engagement Models

Dedicated Development Team
Our developers leverage cutting-edge cognitive technologies to deliver high-quality services and tailored solutions to our clients.

Team Extension
Our team extension model is designed to assist clients seeking to expand their teams with the precise expertise needed for their projects.

Project-based Model
Our project-oriented approach, supported by our team of software development specialists, is dedicated to fostering client collaboration and achieving specific project objectives.
Get Started Today
1. Contact Us
Fill out the contact form protected by NDA, book a calendar and schedule a Zoom Meeting with our experts.
2. Get a Consultation
Get on a call with our team to know the feasibility of your project idea.
3. Get a Cost Estimate
Based on the project requirements, we share a project proposal with budget and timeline estimates.
4. Project Kickoff
Once the project is signed, we bring together a team from a range of disciplines to kick start your project.
Start a conversation by filling the form
All information will be kept confidential.
Insights
Generative AI in asset management: Redefining decision-making in finance
Generative AI is reshaping asset management by incorporating advanced predictive capabilities, fundamentally altering decision-making in finance for more informed investments.
Generative AI in supply chain: Use cases, benefits and development
Incorporating generative AI promises to be a game-changer for supply chain management, propelling it into an era of unprecedented innovation.
From diagnosis to treatment: Exploring the applications of generative AI in healthcare
Generative AI in healthcare refers to the application of generative AI techniques and models in various aspects of the healthcare industry.











